Before I proceed, I want to state that I don’t know Verite’s gender, I didn’t ask. So my references to “he” and “him” are purely an assumption on my part. What I do know as facts is that Verite identifies himself as a hacker and reports that he is a teenager.
Yesterday afternoon (Kiwi time), a user with the twitter handle @V3R1T3 sent me a tweet and asked me to pass on a message to the MODX team because they had “blocked” him. Initially, I wasn’t sure that I wanted to engage in conversation with Verite given that he had publicly admitted to defacing the http://modx.com website and had posted a pastebin with some MODX users account information on the web. However, given these facts, the fact that I run MODX on several sites and have an account at modx.com, and my own innate curiosity, I decided to respond, ask a few questions, and see what I could find out. The resulting conversation was quite interesting and I asked Verite if I could post the chat verbatim on this blog for anyone who might be interested. We chatted for a while on twitter and then moved the conversation to Skype.
To give this conversation some context, I will post a bit of background on the events that led up to it.
A Bit of Background
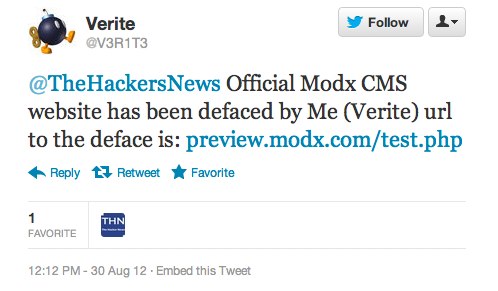
On August 30th, this tweet showed up on my MODX search twitter feed:
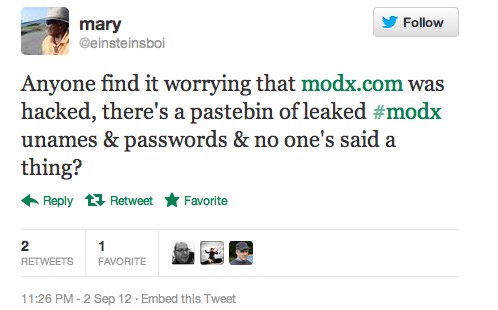
It was followed a few days later by this even more alarming tweet:
Naturally I found this quite worrisome, and since I hadn’t seen anyone else tweeting or saying anything about it, I decided to follow Verite on twitter so I could keep myself in the loop. I also posted on twitter.
This triggered a flurry of tweets and questions, with the eventual reassurance from the MODX team that all data was safe and there was no serious compromise. You can read the official security announcement.
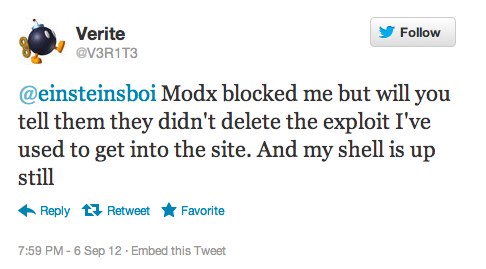
Verite responded on twitter that he had not used an LFI exploit as claimed and posted a couple more tweets. Then, seemingly out of the blue, he sent me this tweet yesterday, which triggered the conversation that follows:
What follows is our conversation and it’s pretty much verbatim. Any edits/omissions are not to change any content or representations but to make it easier to read and follow. In some instances I have merged tweets when they came one after the other for readability.
The Conversation
Verite @V3R1T3 @einsteinsboi Modx blocked me but will you tell them they didn’t delete the exploit I’ve used to get into the site. And my shell is up still
me: @V3R1T3 I’m sure they’ll see your tweet since it has the word #modx in it. But why are you determined to hack the site?
Verite @V3R1T3: @einsteinsboi I’m gathering information, Because of my little attack I’ve managed to find several new 0-day exploits. I’m just wanting to… See how they patch the site and so I can see how I would need to find new 0-day exploits.
me:@V3R1T3 I see. Why so angry at them for blocking u & trying to delete ur exploits & keep you out? Isn’t that what any website owner wld do?… If you hack a site and announce the hack then the owner of the site will try to fix it, right? What do you want them to do?
Verite @V3R1T3: @einsteinsboi I wasn’t mad it was more of me having fun lol. And if they fix it I can see how they fixed it because I own the server… Since I own the server I can see how the edit and apply updates to the Modx website and public scripts thus allowing me to… to know where and when to find a new exploit. But I don’t think they can take me out because I backdoored the scripts. #Modx… And that last tweet I want them to see.
me: @V3R1T3 OK, I think I understand. But why did you target MODX?
Verite @V3R1T3: @einsteinsboi It wasn’t a target. I’m after wordpress and drupal and joomla to. These are public scripts people pay top-dollar for exploits. So I’m just taking out whats easier then I will go after a harder site next. Nothing but business and… Knowledge(:
me: @V3R1T3 OK, so you’re doing it for money and knowledge?
Verite @V3R1T3: @einsteinsboi Yes. If I see they don’t have what I want ill show em where the vulnerability is at. Someone with good IT training can find… And patch it in mere seconds
me: @V3R1T3 Interesting. And would you charge them for this patch? Hey BTW do you mind if I post this chat on my blog as a blog post?
Verite @V3R1T3: @einsteinsboi I don’t mind. Also I would charge them but whats the point? Who knows maybe I will just give the information for free and ask… To be apart of the #Security team. But that’s if I don’t wanna be evil Muahahaha (Nah Jk) I’m just going to leave em alone.
me:@V3R1T3 This has been interesting, thanks for sharing your thoughts with me, and thanks for allowing me to post this chat on my blog… Can you DM me an email address where I can shoot you some more questions to make the post more complete?
Verite @V3R1T3: @einsteinsboi No problem I’m not an evil person I just like to expand my knowledge anyway possible. I will even tell you a secret. I’m a… teenager
{Chat continued on Skype}
Me: So you don’t mind if I share our twitter chat as a blog post?
V3R1T3: It’s all good.
Me: I think a lot of my readers will find it an interesting insight into a hacker’s mind
V3R1T3: Well I’m a very young hacker. So really it might not be what they want but I’ve been into the scene for almost 2 years now. This is just a new alias since I pissed off a few .gov websites.
Me: i understand now from our chat that your attack on MODX site wasnt personal but it sounded like that from some of the tweets you posted
V3R1T3: Well for a minute it got personal because my friend was about to pay me to iFrame the Modx website for a few minutes... But then I actually did get happy because I noticed they patched 1 vuln and deleted my shell. So then I decided to have some fun lol
Me: Why did you disclose on twitter that you had defaced the site and hacked into the db? Wouldn’t it have been better to stay quiet about it till you got the results you desired? Or was it more important to you to see how they patched it?
V3R1T3: I had the site defaced for almost 2 months. I’ve grown tired from the lack of security so I had to make it public. The response time was slow and the patches they did to the deface added more vulns. They logs are easy to get manipulated and the site config.php all goes to the revo-core folder of modx
Me: I see… But the deface was not on the main page, if I recall it was on preview.modx.com or something like that, so is it possible no one was aware of it?
V3R1T3: Lots of people were aware… I just didn’t want the whole world to know yet.
Me: Got it… BTW Please let me know which details of this conversation you don’t want to appear on the blog post
V3R1T3: You can have the whole conversation.
Me: What do you mean when you say you “own their servers” and can see what patches they apply, etc
Me: Is this in reference to the exploits you have in place?
V3R1T3: Yes.
Me: Are these exploits that could be placed on any websites running MODX out there?
V3R1T3: Yes actually. No scanner would find these since it’s a new exploit. If a scanner did find it, then it wouldn’t consider it a threat.
Me: I would completely understand if you don’t answer this question, but what can an ordinary website developer who builds websites using MODX do to protect their sites from being hacked or exploited?
V3R1T3: This is something I NEED to answer because I ask this everyday… Here’s a few steps:
– First he needs to be sure he knows what he’s doing
– All and any templates would be good if he went and looked through the source…. Since the smallest file can lead to a backdoor or exploit.
– NEVER use Nulled software and always try to find a way to keep up with the stats for the site… Like pages accessed… You can do this from some CEO software or that person can own a VPS that he can host his site off of.
And really, I have horrible knowledge in PHP so I can’t say if that’s why Pro’s do.
But basically don’t trust 3rd-party sources.
Modx in this case everysite is vulnerable because of they shell I’ve implanted in the public files.
Me: So are you saying that any new downloads of MODX are vulnerable to attack?
V3R1T3: Yes… No beginner hacker would find them.
Me: hmmm, that’s going to leave quite a few people unsettled
V3R1T3: Yes… It’s a shell the blends in with the 404 page (If they have a custom one)… You need to actually find the salt and manage to decrypt the MD5 .. Which the MD5 is in all symbols.
Me: You mentioned that you’re also planning to target WordPress, Joomla, and Drupal?
V3R1T3: Yes… Just like Modx I will do the same thing… Attack in Silence wait a certain amount of time then if I see no results I will go public… Modx deserved this… Because of the lack of security site information got leaked…. They had a chance to protect all the users but they didn’t keep up in #Security…. Every web designer or publisher (That I know and meant always preform updates to stop things like this)… And as a coder I’m sure you must agree somewhat.
Me: Absolutely. I agree. It’s important to keep your software updated and secure.
V3R1T3: Now you see the reason for the public attack.
Me: In the post they made about the exploit they said that the database you hacked and the data you collected and shared had no passwords?… Did you read that post?
V3R1T3: Yes actually and I spit my soda out from that… Because if you look on twitter multiple people were upset because there PASSWORDS were online… I even tested out the Admin login details.
Me: Apparently this was a dummy password field and the actual passwords were stored elsewhere. So are you saying that there were actual passwords and you were able to use one of them succesfully?
V3R1T3: Yes.
V3R1T3: Dreamhost.com Was hacked by friends of mine who were in Digital-Corruption…. They claimed none of the passwords were real. But what happened? They lost money and the server was rooted. My friends still own dreamhost servers.
Me: Interesting. So here’s the one question that I think a lot of my readers will be anxious to have an answer for. What do you intend to do with the user data you collected, specifically the usernames and passwords? Some people will probably have changed their passwords on other sites and services in fear of other accounts being compromised. Do you intend to exploit this data for financial gain or to compromise other accounts? Or is your only interest in exploiting and hacking the MODX CMS? Do users need to worry about the security of their information?
V3R1T3: Nope… I’m not after them… I want them to see that just because they got a script that everyone loves and uses and that gets updated alot that don’t mean they are protected…. You’re readers need to know that Modx has good security
V3R1T3: But I’m not even a pro… I just have experience. So think what if someone better came along?… BAM tears and angry birds would come after them. This threat should show them that they need to learn MORE about coding so they can KNOW they are protected.
Me: So basically we can consider this an early warning that we need to not trust scripts even if they’re popular?
V3R1T3: Yes… If you noticed it’s only websites that use Modx.com WordPress.org Joomla.com end up getting hacked. I’ve seen at least 20 sites that were coded by a beginner that had no exploits or that had better security.
Me: So a good idea would be for people to learn to code their own sites from scratch?… instead of relying on third party scripts like Joomla, WordPress, Drupal?
V3R1T3: That’s a good idea.
V3R1T3: I’ve seen parts of your blog.
V3R1T3: And that information you give can help.
V3R1T3: And no they can use third party scripts but they need to go through each script and try to find any errors and vulns.….
Me: You mentioned that you’re a teenager and you’ve been doing this for 2 years now? How did you get into hacking?
V3R1T3: Multiple websites of mine got hacked… I started using webs.com. Then ucoz.com.. Then I went into using wordpress and other things like mybb. I was never secure so I spent my time in E-Books learn about hacking.
Me: Do you consider yourself a hacker, hacker-in-training, budding hacker?
V3R1T3: I consider myself a hacker-In-Training
Me: Just trying to think of a title for my post… “Conversation with a _________”
V3R1T3: Even though to most I’m a pro at hacking
Me: And how would you distinguish yourself from what some people call a “script kiddie”?
V3R1T3: No.
V3R1T3: I’m a hacker in training beacause I still don’t know enough… I think I don’t.
Me: What would your response be to someone who referred to you as a script kiddie? I ask this because I know a lot of web developers consider people who plant scripts on servers to be “script kiddies” and “wannabe hackers”. What would your response be to this?
V3R1T3: I’d prove my knowledge. I hate when people call me that. I’m a hacker who tries his best to fight for his own goals.
Me: If the MODX team had engaged with you when you first posted that you had defaced the site, if they had held a dialogue with you to find out how and why you did it, would that have made a difference?
V3R1T3: Maybe. I don’t have no problems. And if they read your blog post then they will see that what I did will only help them in the future… And who knows maybe ill do scans and tell them about any errors. Thats the only good thing about hacks.
Me: Would you recommend that web developers try to engage hackers and learn from them?
V3R1T3: Depending on the hacker. They need to make friends and find someone online they can trust. But if they meet a hacker and become friends, just make sure of one thing
V3R1T3: NEVER
V3R1T3: TRUST
V3R1T3: THE
V3R1T3: DOWNLOADS
Me: Gotcha!
Me: Thanks for your time.
V3R1T3: No problem
And that’s it.
My thoughts
I think one question that a lot of people may have is why did I decide to have this conversation and then post it on my blog? Am I not just giving the hacker what he wants… the spotlight? fame?
Well, that’s a legitimate question, and perhaps legitimate concerns, and may be the subject of another post. I will say this though: ignoring the fact that our sites get hacked, our systems are flawed, and other people sometimes get one over us does not negate the fact that our sites have been hacked, our systems are flawed, and other people do occasionally best us. I do think though that there’s merit in asking questions and trying to understand what’s going on in the mind of the person who decides to break into your site or your software and perhaps something constructive can come out of that dialogue, even if all we get is a bit more information, a bit more knowledge, a bit of understanding about motive. It may inform our future steps and perhaps give us back that sense of control which we all experience when we we’re in the “I don’t know” state.
Dislaimers: I have chosen very intentionally to post this chat and events as is without adding my own thoughts and opinions regarding the information shared by all parties here, whether we should worry, etc etc. I leave it to you to make up your own mind.
I look forward to your comments, questions, and hellos 🙂

Interesting read, thanks for sharing.
awesome post
#modx find/close those doors
don’t b complacent
I agree.
Mary,
First of all thanks for doing this I’m sure some people might not like it but it’s just something we have to deal with and learn from.
I think you should mention that users need to upgrade to the latest version of MODX which takes care of a security issue, I’m not sure if we can believe what a hacker says 100% but we do have to give it some credibility.
I do like the fact that the hacker mentions that MODX does have good security.
Again nothing is 100% secure if it’s on the internet so these things are bound to happen to any CMS this only means MODX is getting more popular and this just comes with the territory.
Anyways thanks for the write up very insightful and informative.
Ben
I’m not sure that upgrading to the latest version IS the solution to this problem. If you read the latest MODX security post on the forums (http://forums.modx.com/thread/79153/modx-website-compromise-update-revolution-still-safe#dis-post-436167), Jay says:
However, keeping software updated should always be a priority. And again, my intent in this post was not to offer any opinions or advice, just to post the information I had obtained.
I’m not sure that he said MODX has good security. I think his exact words were “…updates don’t mean they’re protected. Your readers need to know that MODX has good security”, i.e. they need to be reassured that the product they’re using is safe, and at the moment it’s not, according to him anyway. And yes, nothing is 100% secure, but I think we tend to forget that. I subscribe to the Drupal security feed and I get notifications very very frequently of vulnerabilities, with details about each vulnerability and what the severity is, and the risks, and I can then act on my sites with that information. I think the important lesson here is to not bury our heads in the sand and be so gung-ho about the positives while ignoring or hushing up the negatives.
Thanks for your feedback
mary
Very interesting! Thank you for sharing!
Ask him how much he wants for the exploit, I wouldn’t mind paying for it if it is within my means to do so. My real email was entered in the quip form.
Ben
I’m hoping that he’ll come on here and perhaps respond to some of the questions himself. My intention is not to act as an intermediate between him and MODX, so I do hope he responds directly himself.
mary
One thing that I realized is that this hacker had no tolerance for people beeing not as smart as him or having all the knowledge in place they need to be “secure”.
He is comparing himself (one huge and complicated topic) to “us” – people with at least 5 big topics the need to know all about if they work in the web (als mostly self emploed).
Feeling superior because of knowledge is ok and natural. Playing with that knowledge is not nice. I hope he’ll get it some day. And still I look up to him, because he is smarter than me in the one topic he chose. I dont like people beeing smarter than me 🙂
Guido, that’s a very insightful comment. The sense I got from him however is quite different. He feels he doesn’t know enough, and that actual programmers should know better. His point about what if a better programmer/hacker than him had come along and discovered these exploits was one I found quite interesting.
I think the challenge for all of us is to work to become smarter, to be one step ahead, and to always be learning…. at least that’s what I got from it.
And yes, I feel you on the people being smarter than me comment… LOL
mary
I’m glad you did, and personally I was thinking the same thing why had no one from the ModX team engaged them, what possible harm could come from at least acknowledging them when its already made public, certainly would have made me feel better.
As most we always look at reports for security of systems as run by scripting and testing software, the biggest lesson here is that those will never find 100% of your threats like a person with a brain.
I’m glad that at least we can learn more from this case as a community and maybe this is a begining to an even better security measures for ModX.
I’ve also added these few things to the htaccess file to help somewhat protect the configuration file and htaccess files.
NOTE: Please remove the spaces after the tag. They’re there just there to prevent WP from trying to process the code
#Protect the .htaccess File
< files .htaccess="" >
order allow,deny
deny from all
< /files >
#Protect the configuration file
< filesMatch "config\.core\.php$" >
order allow,deny
deny from all
< /filesMatch >
AGAIN: Please remove the spaces after the < tag and before the > tag. They’re there just there to prevent WP from trying to process the code
Thanks for the comment Charles, and thanks for the security tips. I’m a firm believer that you can’t go wrong having an honest conversation 🙂
mary
CharlesMx, mind adding that little bit to the documentation on hardening ModX?
sure, once added I”ll update here as well
Many months ago I downloaded some e-books about hacking to learn about security because I felt vulnerable due to my lack of knowledge.
I guess now I’ll actually have to read them.
Mary,
Great job on the post, The conversation and details were great, Also to everyone I know you guys may not trust me but none of your websites will be at risk. Once I talk to the Modx admin (Later Today or Tomorrow) I will show him the exploits I’ve found in his site. By then end of this months the underground-severe exploit’s I’ve found will be patched ASAP. Also @Ben I don’t plan on selling the exploit but I can scan any sites you own and such for some money. Or I can give you small exploits that can’t damage any modx website in any way possible.
Hey Dude,
maybe we can help each other out here. Your website could use some fresh paint 🙂
Really really interesting stuff. Dialogue with hackers around modx security can only be a good thing. Obviously, we’re worried about our favourite CMS but the end result of this would be an even more secure platform.
Is there a dedicated modx security role / person? As modx ‘grows up’ and becomes more popular, this scenario is going to be common.
Kudos to Mary for a great writeup. Many things have happened behind the scenes, and we’re taking this very seriously. At the moment, we’re continuing to document the facts before posting a debrief on our blog—we want to make sure we can tell the full story. Also, credit is due to V3R1T3, as we got the not-so-gentle nudge that made us pay attention to the main site again.
If I may ask, why did you block him on twitter, then? That struck me as not very helpful in finding out more about the hack.
I sure didn’t block him at all. In fact we’re having a dialog right now.
Thanks for clearing this up, that’s great to hear. Must have misinterpreted the “@V3R1T3 sent me a tweet and asked me to pass on a message to the MODX team because they had “blocked” him.” part of the story.
Blocked the IP address(es) from being able to continue attempting any exploits on the server.
To provide a postmortem, here’s the results of the detailed analysis that began last week. Thanks for everyone’s patience during our “quiet period” http://modx.com/blog/2012/09/11/modx-security-breach-facts-fiction-and-future/
Sounds like a typical teenager randomly defacing websites for personal amusement. I hate such people with a passion.
I think the developers should focus on security in future releases! In Evo 1.0.6 there was a vuln which made possible uploading php-shells in the modx-cache directory. I had around 20 Websites in the modx.com Showcase-gallery and EACH of those sites, which was listed there was victim of an uploaded shell! I mentioned this to one of the head-devs of modx and told them to remove all my entrys out of the modx-showcase! They removed my showcase entrys but never published this info to the public/the users who had an entry in the showcase-galery. THIS ISNT COOL! So in my point of view their statements on hacks or vulns arent credible so far. A pwned website or various websites could mean bankrupt for us developers! Take care…
I know this thread is a little out dated but I am confused why there is any respect being forwarded to this person at all. A Hacker this person is not. They are not worthy of the title and it’s very offensive to those of us who are. Script kiddie or cracker is more appropriate and there’s nothing but shame attached to those terms. Just because one is able to break into someone else’s house doesn’t mean they should. Much less, do so and have the audacity to announce the act with the expectation of gratitude or fiscal gain! That is nothing more than mere childish stupidity and they deserve to to pay for their trespass.
Maybe this V3R1T3, who chooses to hide in their anonymity and obviously has some talent, will eventually grow their skills and understand what it truly means to be a hacker. Hopefully before they earn 5 to 10 and cheat all of us of their talents and contributions to the industry.
.
.
. . .
BTW. For you my friend.
http://www.catb.org/~esr/faqs/hacker-howto.html